
Unleashing ATO Defense: How AuthSafe Secures Your Email
Email security is crucial in ATOs (Account Takeover) since it protects information systems from cyber threats and potential security breaches. ATOs are granted to IT systems that fulfill strict security and privacy standards, and guaranteeing the security of email exchanges is an important part of the authorization process.
With its sophisticated detectors, Authsafe efficiently addresses the issues of Email Safety, offering comprehensive protection against fraudulent activity and other security threats. Here are some of the reasons why Email Safety and Authsafe’s detectors are critical components of ATOs:
- Preventing Phishing Attacks: Phishing attacks are among the most common cyber threats, where attackers use deceptive emails to trick users into revealing sensitive information or gaining unauthorized access. Authsafe’s detectors, such as” Disposable Email,” Domain Not Registered,” and” Invalid Domain Email,” are designed to detect suspicious email domains and prevent users from falling victim to phishing attempts. By blocking emails from disposable and unregistered domains, Authsafe significantly reduces the risk of phishing attacks.
- Enhancing Authentication Security: Authsafe’s” Invalid Email” detector ensures that only valid email addresses are accepted during registration or login attempts. This helps in maintaining the integrity of user accounts and preventing misuse of the authentication process. By validating email formats, Authsafe ensures that only legitimate users can access the system, reducing the risk of unauthorized access.
- Detecting Spoofing Attempts: Cybercriminals often use slightly modified email addresses to deceive users and gain access to sensitive information. Authsafe’s” Email Not Similar” detector employs advanced algorithms to compare email addresses for similarities and promptly detects potential spoofing attempts. By identifying suspicious activities, Authsafe prevents fraudulent access and mitigates the risk of account compromise.
- Blocking Disposable Email Addresses: Disposable email addresses are temporary and often used to create fake accounts or evade verification procedures. Authsafe’s” Disposable Email” detector maintains a comprehensive database of known disposable email providers and blocks registration or communication attempts using these addresses. This proactive approach ensures that only genuine users with valid email addresses can access the system.
- Real-Time Threat Detection: Authsafe’s detectors operate in real-time, constantly monitoring email communications and user activities. Timely detection of suspicious email behaviors allows Authsafe to respond swiftly to emerging threats and potential security breaches, mitigating risks before they escalate.
- Integration with Threat Intelligence Feeds: Authsafe integrates with threat intelligence feeds, providing users with up-to-date information about emerging threats and known malicious email ad- dresses. By leveraging threat intelligence, Authsafe enhances its email safety capabilities and informs users about potential risks.
Protecting What Matters: Our Policy Signals to Thwart ATO Attacks
AbnormalEmailSyntax: Detecting Invalid Email Addresses
The AbnormalEmailSyntax algorithm is designed to detect invalid email addresses based on their syntax. Email addresses are essential for online communication, and ensuring their validity is crucial for a secure experience. Let’s understand how this algorithm works:
- Syntax Validation: The algorithm first checks the event type to ensure it is either” login succeeded” or” logout.” Then, it extracts the user’s email (ue) associated with the event.
- Syntax Check: The algorithm performs a syntax validation on the email address using a custom implementation, removing the dependency on third-party libraries.
- Invalid Email Detection: If the email syntax is invalid, the algorithm raises an event called” Ab- normalEmailSyntax” (AES) and assigns a score to indicate the severity of the issue.
- Real-Time Protection: AbnormalEmailSyntax operates in real-time, continuously monitoring email addresses for syntax errors. The user is notified to take necessary action if an invalid email is detected.
It Matters to You: Know Why?
The AbnormalEmailSyntax algorithm plays a critical role in safeguarding your online communications. Here’s why it matters:
- Early Detection of Invalid Emails: The algorithm helps prevent email-related issues, such as bounced emails or delivery failures, by identifying invalid email addresses.
- Mitigating Security Risks: Invalid email addresses could be used to exploit communication channels or gain unauthorized access to accounts. The algorithm helps mitigate such security risks.
- Ensuring Reliable Communication: By ensuring that email addresses have correct syntax, the algorithm helps ensure smooth and reliable communication with recipients.
Email Domain-Based Policy Signals
AbsentDomainRegistrar: Detecting Absent Domain Registrars
The AbsentDomainRegistrar algorithm focuses on validating domain registrar information. Domain registration information is crucial for verifying a website’s or email domain’s legitimacy. Here’s how this algorithm works:
- Syntax Validation: The algorithm first checks the event type to ensure it is either” login succeeded” or” logout” and extracts the user’s email address (use) from the event.
- Email Syntax Check: The algorithm performs a syntax validation on the email address to ensure it follows the correct format.
- Domain Registrar Validation: The algorithm will validate the domain registrar information using the WHOIS database if the email syntax is valid.
- Absent Domain Registrar Detection: If the domain registrar is not found for the provided email domain, the algorithm raises an event called” AbsentDomainRegistrar” (ADR) and assigns a score to indicate the significance of the absence.
- Real-Time Protection: The AbsentDomainRegistrar algorithm operates in real-time, continuously monitoring email addresses’ domain registrar information. The user is notified to take necessary action if an absent domain registrar is detected.
It Matters to You: Know Why?
The AbsentDomainRegistrar algorithm ensures the authenticity and security of email communications and website interactions. Here’s why it matters:
- Domain Verification: The algorithm helps verify the legitimacy of email domains, preventing potential phishing or spoofing attempts.
- Identifying Suspicious Emails: The absence of a domain registrar can indicate suspicious or unauthorized email domains, alerting users to be cautious about potential threats.
- Protecting Against Cyberattacks: The algorithm enhances protection against cyberattacks and email-based security risks by detecting domains without proper registration.
AbsentSPFRecord: Detecting Absence of SPF Record
The AbsentSPFRecord algorithm detects the absence of SPF (Sender Policy Framework) records. SPF records help prevent spam, ensuring emails are sent from legitimate sources. Here’s how this algorithm works:
- Syntax Validation: The algorithm first checks the event type to ensure it is either” login succeeded” or” logout” and extracts the user’s email address (use) from the event.
- SPF Record Check: The algorithm validates the email’s domain for SPF records using DNS queries. It checks whether the domain has an SPF record (v=spf1) in its DNS TXT records.
- Domain Security Check: The algorithm further validates domain security using the” checkd- marc” library to check for potential spoofing risks associated with DMARC and SPF.
- Absent SPF Record Detection: If an SPF record is not found or if domain security checks indicate potential spoofing risks, the algorithm raises an event called” AbsentSPFRecord” (ASR) and assigns a score to indicate the significance of the absence.
- Real-Time Protection: The AbsentSPFRecord algorithm operates in real-time, continuously monitoring email addresses for the presence of SPF records. The user is notified to take necessary action if an absent SPF record is detected.
It Matters to You: Know Why?
The AbsentSPFRecord algorithm protects your email communications from potential email spoofing and phishing attempts. Here’s why it matters:
- Preventing Email Spoofing: SPF records help prevent malicious actors from impersonating your email domain, ensuring that only authorized servers can send emails on your behalf.
- Enhanced Email Security: The absence of SPF records can indicate potential vulnerabilities in your email domain, making it easier for attackers to spoof your identity.
- Mitigating Phishing Risks: By detecting and alerting you about missing SPF records, the algorithm helps you take proactive measures to mitigate phishing risks and unauthorized email activities.
The AbsentSPFRecord algorithm is crucial in Authsafe’s real-time threat detection capabilities. Detecting the absence of SPF records helps protect your email communications from spoofing and phishing risks, ensuring a safer and more secure email experience.
ExpiredDomain: Detecting Expired Domains
The ExpiredDomain algorithm is designed to detect and alert users about expired domains associated with email addresses. Expired domains can be susceptible to misuse and pose security risks. Here’s how this algorithm works:
- Syntax Validation: The algorithm first checks the event type to ensure it is either” login succeeded” or” logout” and extracts the user’s email address (use) from the event.
- Domain Expiry Check: The algorithm uses the” whois” library to query domain information and determine the domain’s expiration date associated with the email address.
- Expiry Date Calculation: If the domain’s expiration date is within 60 days, the algorithm raises an event called” ExpiredDomain” (ED) and assigns a score to indicate the significance of the expiry. It also notifies the user about the remaining days until the domain expires.
- Real-Time Protection: The ExpiredDomain algorithm operates in real-time, continuously monitoring email addresses for domain expiry. The user is notified to take necessary action if an expired domain is detected.
It Matters to You: Know Why?
The ExpiredDomain algorithm is crucial in identifying potential security risks associated with expired domains. Here’s why it matters:
- Preventing Security Vulnerabilities: Expired domains may become vulnerable to misuse, phishing attacks, or domain hijacking, posing security risks to your online presence.
- Proactive Domain Management: By detecting and alerting you about domain expiration, the algorithm helps you take proactive measures to renew or secure your domain to prevent potential security breaches.
- Maintaining Business Reputation: Timely renewal of domains ensures that your online services, email communication, and web presence remain functional, maintaining a positive business reputation.
5. Disposable Email: Detecting Disposable Email Addresses and Why it Matters for You
The DisposableEmail algorithm detects and alerts users about disposable email addresses, which are temporary and often associated with spam or malicious activities. Detecting disposable email addresses can help prevent misuse and maintain the integrity of your user database. Here’s how this algorithm works:
- Syntax Validation: The algorithm first checks the event type to ensure it is either” login succeeded” or” logout.” It then extracts the user’s email address (use) from the event and identifies the domain.
- Domain Validation: The algorithm tests the email address domain for the presence of MX, NS, and SPF records. It uses DNS resolution to check if the domain has valid mail exchange (MX) and nameserver (NS) records. It also verifies if the domain has a Sender Policy Framework (SPF) record used for email authentication.
- Disposable Domain Detection: The algorithm compares the domain against a list of known dis- posable email domains. It also checks for keywords or patterns commonly found in disposable email addresses. If a match is found, the algorithm raises an event called” DisposableEmail” (DE). It assigns a score to indicate the significance of the detection.
- Real-Time Protection: The DisposableEmail algorithm operates in real-time, continuously monitor- ing email addresses for disposable domains. The user is notified to take necessary action if a disposable email address is detected.
It Matters to You: Know Why?
The DisposableEmail algorithm is crucial for maintaining the integrity of your user database and preventing potential security risks.
- Preventing Spam and Malicious Activities: Disposable email addresses are often used for spamming, phishing, and other malicious activities. Detecting and filtering out disposable emails can help reduce such risks.
- Protecting User Data: By filtering out disposable email addresses, the algorithm ensures that genuine and valid user data is collected, enhancing the quality and reliability of user information.
- Maintaining Database Quality: Filtering out disposable email addresses helps maintain a clean and reliable user database, improving communication efficiency and user engagement.
- Preventing Misuse of Services: Blocking disposable email addresses can deter users from creating multiple accounts for fraudulent purposes or taking advantage of free services.
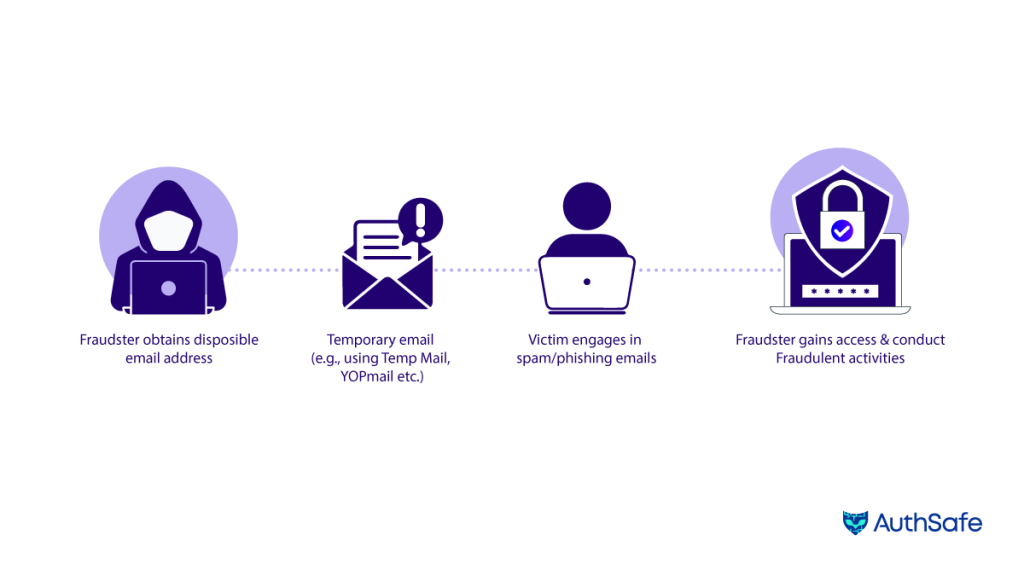
ManyDigitsInUsernameEmail: Detecting Emails with Many Digits in Username and its Significance
The ManyDigitsInUsernameEmail algorithm aims to detect email addresses with excessive digits in the username part, which may indicate suspicious or unauthentic email addresses. Detecting such email addresses can help identify potential security threats and enhance the system’s overall security. Here’s how the algorithm works:
- Syntax Validation: The algorithm checks the event type to ensure it is either” login succeeded” or” logout.” It then extracts the user’s email address (ue) and username (un) from the event.
- Digit Count: The algorithm counts the number of digits in the username and the email address (before the” @” symbol).
- Threshold: The algorithm defines a threshold (currently set to 9) to determine the maximum allowed digits. Suppose the digit count in the username or the email address exceeds the threshold. In that case, the algorithm raises an event called” ManyDigitsInUsernameEmail” (MDIUE). It assigns a score to indicate the significance of the detection.
- Real-Time Protection: The ManyDigitsInUsernameEmail algorithm operates in real-time, continuously monitoring email addresses for the presence of many digits. If an email address with many digits is detected, the user is notified to take necessary action.
Significance of Detecting Emails with Many Digits in Username
The ManyDigitsInUsernameEmail algorithm plays a vital role in identifying potential security risks and improving the overall security posture of your system. Here’s why it is significant:
- Identifying Suspicious Activity: Email addresses with excessive digits in the username may indicate suspicious or fraudulent behavior. Detecting such email addresses early can help prevent potential security breaches.
- Improving Account Security: The algorithm helps identify potential weak points in user account security by identifying email addresses that deviate from standard naming conventions.
- Reducing Spam and Phishing: Many digits in email addresses are often associated with temporary or disposable email accounts used for spamming or phishing. Detecting such emails can help reduce the risk of spam and phishing attacks.
- Enhancing Data Quality: Filtering out email addresses with many digits can help maintain a clean and reliable user database, enhancing the accuracy and quality of user information.
Enhancing Phone Number Security: Defending Against ATO
Authsafe offers a variety of strategies to provide phone safety and improve phone number security. In Authsafe, phone safety is concerned with checking the validity and authenticity of phone numbers used during registration, authentication, or other user interactions. The purpose is to prevent fraudulent actions, unauthorized access, and account takeovers linked to compromised or forged phone numbers. Here’s a more in-depth description of how Authsafe provides phone security. SIM switching is a scam in which criminals obtain control of your phone number by tricking your carrier into linking it to a SIM card they own. They get personal information through phishing and social engineering, allowing them to effectively imitate you. They intercept your calls and messages after convincing the carrier to activate a new SIM card on their handset. This fraud can result in unauthorized access to your accounts and large financial losses. Avoid phishing attacks using strong passwords and adopting authentication methods other than your phone number.
According to a Federal Bureau of Investigation (FBI) study, the number of reported SIM switch frauds is rising. The FBI received 1,611 complaints of SIM swaps in 2021, resulting in losses of more than $68 million. When compared to prior years, this constituted a huge rise. The FBI received only 320 SIM swap complaints between January 2018 and December 2020, with victims losing around $12 million. These figures demonstrate the rising worry and financial effect of SIM switch fraud on consumers and corporations. [1]
Explore the capabilities of our Phone Number Based Policy Signals.
8. AbnormalPhoneNumberSyntax: Detecting Emails with Many Digits in Username and its Significance
The AbnormalPhoneNumberSyntax class is designed to be part of a larger framework for detecting abnormal behavior and security-related events. It checks the phone number’s syntax and determines if it is valid and possible. If the phone number is invalid, it generates an event named’ APNS’ with a score indicating the abnormality’s severity. The code uses the phone numbers library, which is a third-party library for working with phone numbers and their validation.
- Syntax Validation: The algorithm checks the event type to ensure either” register succeeded” or” login succeeded.” It then extracts the user’s phone number from the event.
- Phone Number Validation: The algorithm ensures that the phone number starts with a” +” and validates it using the phone numbers library. If the phone number’s length is incorrect (less than ten or greater than 15), the algorithm raises an event called” APNS.” It assigns a score to indicate the significance of the detection.
- Possible and Valid Numbers: According to the phone numbers library, the algorithm checks if the phone number is both a possible and valid number. If the phone number is valid and possible, no event is raised. Otherwise, the algorithm raises the” APNS” event with a corresponding score.
- Real-Time Protection: The AbnormalPhoneNumberSyntax algorithm operates in real-time, continuously monitoring phone numbers for invalid syntax. The user is notified to take necessary action if an invalid phone number is detected.
It Matters to You: Know Why?
The AbnormalPhoneNumberSyntax signal is important for your system’s security and protection against potential ATO (Account Take Over) attacks. Here’s why it matters to you:
- Enhanced Account Security: By detecting invalid phone numbers with suspicious syntax, Authsafe ensures that only legitimate and authorized users gain access to their accounts. This helps enhance the overall security of user accounts and prevents unauthorized access attempts.
- Preventing ATO Attacks: ATO attacks significantly threaten your system’s integrity and user data privacy. The AbnormalPhoneNumberSyntax signal prevents ATO attacks based on invalid or compromised phone numbers. By detecting and blocking phone numbers with excessive digits or incorrect syntax, Authsafe effectively thwarts potential ATO threats.
- Real-Time Protection: The AbnormalPhoneNumberSyntax algorithm operates in real-time, continuously monitoring phone numbers for anomalies. This immediate detection and notification system allow you to take prompt action when suspicious phone numbers are detected, mitigating potential risks before they escalate.
- Maintaining Data Quality: By filtering out invalid phone numbers, Authsafe ensures the accuracy and reliability of user information within your system. This maintains a clean and dependable user database, enhancing data quality and usability.
- Reducing Fraudulent Activities: Phone numbers with suspicious syntax are often associated with fraudulent activities, such as fake account registrations or phishing attempts. The AbnormalPho- neNumberSyntax signal helps reduce the risk of fraud by identifying and blocking such phone numbers.
- User Trust and Confidence: Implementing robust security measures, such as the AbnormalPho- neNumberSyntax algorithm, builds user trust and confidence in your system. Users feel reassured that their accounts and sensitive information are protected from security threats.
- Comprehensive Security Framework: The AbnormalPhoneNumberSyntax signal is integral to Authsafe’s comprehensive security framework. By combining various security algorithms and measures, Authsafe ensures a layered defense system that guards against various security risks, including ATO attacks.
Detecting Disposable Phone Numbers
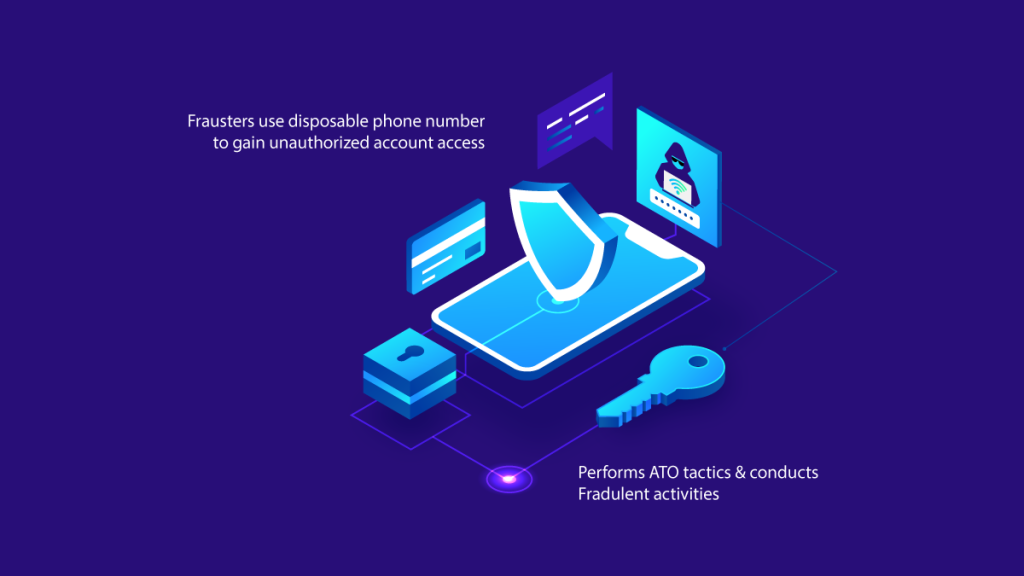
The DisposablePhone algorithm specializes in detecting disposable phone numbers commonly used for fraudulent activities. Authsafe uses a database of disposable phone numbers, and this algorithm efficiently checks if a phone number is present in the database. Let’s explore the added value of this algorithm in more detail:
- Enhanced Security Against Phishing Attempts: Phishing is a prevalent cyber threat where attackers attempt to deceive users into revealing sensitive information through fake websites or emails. Disposable phone numbers are often used in phishing attacks to create temporary communication channels. By identifying and blocking disposable phone numbers, the DisposablePhone algorithm acts as a shield, protecting users from falling victim to phishing attempts.
- Preventing Account Takeover (ATO) Attacks: In an ATO attack, malicious actors attempt to gain unauthorized access to user accounts. Disposable phone numbers may be used to create fraudulent accounts or to bypass two-factor authentication mechanisms. The DisposablePhone algorithm plays a crucial role in ATO prevention by identifying and blocking suspicious phone numbers associated with such attacks.
- Safeguarding Sensitive Data: Disposable phone numbers are often associated with temporary and anonymous communication channels, making them attractive for attackers seeking anonymity during malicious activities. The DisposablePhone algorithm safeguards sensitive user data from potential breaches by actively detecting and blocking these disposable numbers.
- User Confidence and Trust: The DisposablePhone algorithm within Authsafe’s security framework instills confidence in users that their accounts are protected against fraudulent activities. Knowing that disposable phone numbers are being actively monitored and blocked creates a sense of trust in Authsafe’s commitment to user safety and data protection.
- Seamless User Experience: While the DisposablePhone algorithm works diligently behind the scenes to detect and prevent threats, Authsafe users experience a seamless and uninterrupted online journey. The algorithm’s real-time detection capabilities ensure that potential risks are addressed promptly without causing any inconvenience to users.
- Compliance with Security Regulations: Organizations must adhere to strict security regulations and data protection standards in many industries. By incorporating the DisposablePhone algorithm, Authsafe demonstrates its commitment to maintaining a secure environment that aligns with these regulatory requirements, thereby building trust with users and regulatory bodies.
- Staying Ahead of Evolving Threats: Cyber threats constantly evolve, and attackers find new ways to exploit vulnerabilities. The DisposablePhone algorithm’s dynamic approach and continuous monitoring allow Authsafe to stay ahead of emerging threats, adapting its security measures to counter ever-changing attack techniques effectively.
- Proactive Risk Mitigation: By proactively detecting and blocking disposable phone numbers, Authsafe prevents potential security incidents before they can escalate into full-blown breaches. This proactive risk mitigation approach significantly reduces the impact of security threats on users and the platform.
It Matters to You: Know Why?
- Reducing Fraudulent Activities: Disposable phone numbers are often associated with spamming, phishing, and fake account registrations. Authsafe’s DisposablePhone algorithm helps reduce the risk of fraudulent activities by identifying and blocking disposable phone numbers.
- Real-Time Detection: The algorithm continuously monitors phone numbers for disposable characteristics in real-time. Upon detecting a disposable phone number, you receive immediate alerts, enabling you to take necessary precautions and safeguard your account.
- Improved Account Security: By blocking disposable phone numbers, Authsafe enhances the overall security of user accounts. This contributes to a trustworthy and safe user experience within the Authsafe platform.
- Combating ATO Threats: Preventing the use of disposable phone numbers is a proactive approach to combat ATO threats. Authsafe’s DisposablePhone algorithm adds an extra layer of protection, reducing the risk of unauthorized access attempts and account compromises.
The DisposablePhone algorithm plays a vital role in Authsafe’s ATO protection strategy, providing robust security measures to ensure the authenticity and safety of user accounts. By detecting and blocking disposable phone numbers associated with fraudulent activities, Authsafe protects its users from potential security breaches and unauthorized access attempts. With real-time monitoring and proactive measures, Authsafe empowers users to maintain control over their accounts and enjoy a secure online experience within the Authsafe platform.
Take the first step towards a more secure future. Try AuthSafe today and experience the peace of mind that comes with having a robust fraud detection solution by your side.
References
[1] Norton, “Sim swap fraud: How to prevent it and stay safe,” https://us.norton.com/blog/mobile/sim- swap-fraud, Year, accessed: July 28, 2023.



