
IP Safety: The First Line of Defense in Cyber Space
IP safety refers to the steps taken to ensure the security and integrity of a company’s network and systems by monitoring and controlling IP addresses and their associated activities. These addresses are unique numerical IDs allocated to network devices, and they are critical in facilitating communication and data exchange over the internet. Malicious actors, on the other hand, frequently use IP addresses to perform cyber assaults such as unauthorised access attempts, phishing, and distributed denial-of-service (DDoS) attacks.
What Does IP Safety Means?
IP safety confronts various issues due to the dynamic nature of IP addresses and the increasing strategies utilised by hackers. Traditional security measures may not be adequate to detect and respond to real-time threats effectively.Facebook has been hacked, exposing the personal information of nearly 50 million users. The attackers exploited three software flaws in Facebook’s systems, and could have gained access to apps like Spotify, Instagram, and hundreds of others. Facebook has fixed the vulnerabilities and notified law enforcement officials, but the company is still investigating the scope of the attack and the identity of the attackers. This is the latest in a series of scandals for Facebook, which has been criticized for its handling of user privacy. Among the difficulties are the following:
- IP Spoofing: Attackers can disguise their real IP addresses using IP spoofing techniques, making it challenging to trace the true source of the attack.
- Botnets: Botnets are networks of compromised devices controlled by a single entity. These botnets can generate large-scale attacks with multiple IP addresses, making them harder to detect.
- Fast Geolocation: Attackers may change their geolocation rapidly to evade detection and launch attacks from different locations.
- Dynamic IP Assignment: Many internet service providers (ISPs) use dynamic IP addressing, which means that IP addresses are frequently reassigned to different users. This can hinder accurate attribution of malicious activities to specific individuals.
How Authsafe Helps Identify Real-Time Threats?
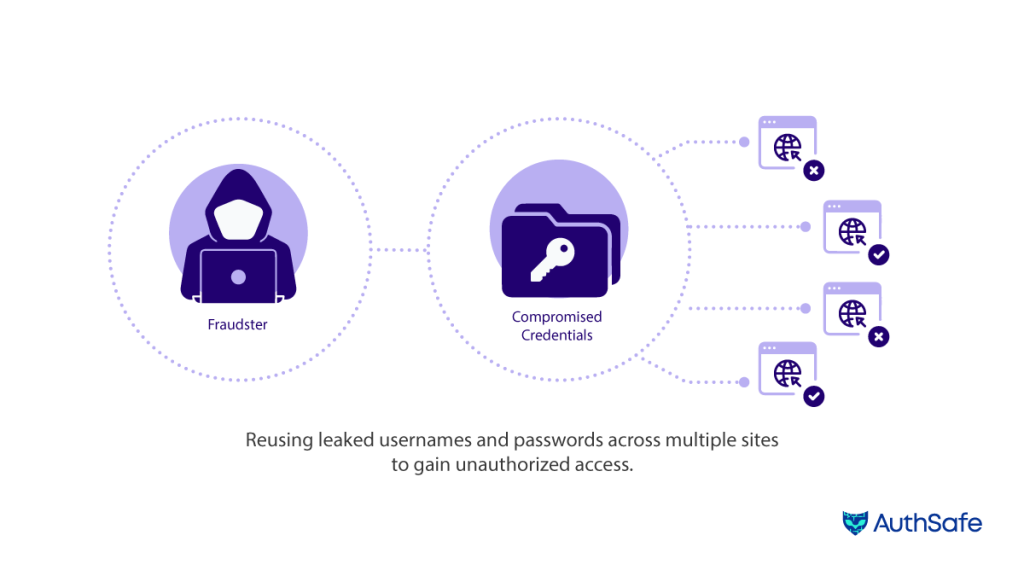
Authsafe addresses the challenges of IP safety by providing real-time threat detection and monitoring solutions. Here’s how Authsafe helps users identify and respond to threats:
Authsafe maintains a comprehensive IP reputation database that continuously updates and tracks the reputation of IP addresses, flagging known malicious IPs and suspicious geolocations, making it easier to identify potential threats with lightning-fast response leveraging GraphCE package developed by Authsafe team incorporating Radix tree data structure. Authsafe profiles the behaviour of legitimate users and devices to establish baseline patterns, and deviations from these patterns trigger alerts for potential security breaches. It employs advanced machine learning algorithms to analyse IP behaviours and detect anomalies, identifying unusual patterns, such as rapid geolocation changes or unusual traffic, which may indicate malicious activities.
Additionally, Authsafe uses behaviour analysis and threat intelligence to identify devices that are part of botnets or participating in coordinated attacks, helping users mitigate large-scale threats. Furthermore, Authsafe provides real-time monitoring of IP activities, enabling users to respond swiftly to emerging threats, and timely detection allows organisations to take proactive measures to mitigate potential risks before they escalate. Authsafe also integrates with threat intelligence feeds, enabling users to access up-to-date information about emerging threats and known malicious IPs. Moreover, Authsafe can be configured to trigger automated responses based on identified threats, such as flagging malicious IP addresses or redirecting suspicious traffic for further analysis.
IP based Policy Signals
FastGeoLocation: Detecting Suspicious Location Changes and why it matters for you
Imagine you have a smart device or computer connected to the internet. Whenever you use your device, it leaves a digital trail called logs that contain information like your location, the time of your activity, and more. These logs can be valuable for monitoring your device’s security.
FastGeoLocation is an essential tool in keeping your online experiences safe. It focuses on detecting rapid changes in your device’s location, which may indicate suspicious or potentially harmful activities. Here’s how it works:
- Calculating Speed: FastGeoLocation calculates how fast your device moves from one place to another based on your location logs. By measuring the distance traveled and the time between two locations, it figures out the speed.
- Event Detection: If the calculated speed is higher than a certain critical threshold, it raises a security “flag” or event called “Fast Geolocation” (FG). This flag tells us that there has been a swift change in your device’s location, which can be a sign of possible security risks.
- Staying Alert: When the Fast Geolocation event is detected, it means that your device’s location changed unusually fast. This might be due to someone trying to access your account from a different location or even an attempt to deceive the system.
- Real-Time Protection: FastGeoLocation works in real-time, constantly monitoring your device’s logs to detect any suspicious activities promptly. If a fast geolocation change is detected, you’ll receive a notification to stay alert and take necessary action.
MismatchedIPTimestampTZ: Verifying Timezone of IP and Timestamp
When you engage with websites, applications, or online services in the digital world, they maintain records called logs. These logs contain vital information about your activity, such as your IP address (where you are online) and timestamps (when you performed something). This data is important for security, but it must be validated to verify its accuracy and safety.
The MismatchedIPTimestampTZ algorithm acts as a detective, investigating logs to ensure that everything matches up appropriately. This is how it works:
- Validation of Timezones: The algorithm checks if the timezone of your IP address matches the timezone recorded in your timestamps. If they don’t match, it raises a security concern.
- Event Detection: If the algorithm finds a mismatch between the IP timezone and the timestamp timezone, it raises a special event called “Mismatched IPTZ” (MITT). This event signals a potential problem with the authenticity of your online activities.
- Real-Time Protection: MismatchedIPTimestampTZ works in real-time, constantly examining your logs to detect any timezone discrepancies promptly. If it detects any inconsistencies, you’ll receive a warning to stay vigilant.
Why it’s Crucial for You?
The MismatchedIPTimestampTZ algorithm is crucial for protecting your online identity and activities. Here’s why it matters:
- Preventing Unauthorised Access: By verifying that your IP location matches the timestamp location, the algorithm helps detect any unauthorised access attempts. It ensures that someone isn’t pretending to be you from a different location.
- Guarding Against Phishing: Mismatched timezones can be a sign of potential phishing attempts or fraudulent activities. The algorithm acts as a guardian, keeping your online experiences safe from such threats.
- Alerting for Suspicious Activities: With real-time protection, the algorithm alerts you to any discrepancies immediately. This way, you can take action and secure your accounts before any potential harm occurs.
IP Based Policy Signals
MismatchedIPPhoneLocation: Verifying IP and Phone Number Location
The MismatchedIPPhoneLocation algorithm is designed to validate the location of an IP address and a phone number associated with an event. This process is crucial to ensure the authenticity and security of online activities. Let’s understand how it works:
- Validation of Phone Number: The algorithm first checks the event type to ensure it is either “register succeeded” or “login succeeded.” Then, it extracts the phone number associated with the event and verifies its presence. If the phone number is missing, the algorithm disregards the event.
- Validation of IP Address: Next, the algorithm examines the event for the presence of an IP address. If an IP address is missing, the event is ignored.
- IP and Phone Number Location Comparison: The algorithm proceeds to validate the locations of both the IP address and the phone number. It leverages external services to obtain location data for the IP address and utilises phonenumbers library to obtain the country code for the phone number.
- Detection of Mismatch: The algorithm compares the country codes of the IP address and the phone number. If they do not match, it raises an event called “MismatchedIPPhoneLocation” (MIPL), indicating a mismatch between the IP and phone number locations.
- Real-Time Protection: MismatchedIPPhoneLocation operates in real-time, promptly detecting any discrepancies between IP and phone number locations. If a mismatch is detected, the user receives a notification to take necessary action.
Why it’s Crucial for You?
The MismatchedIPPhoneLocation algorithm plays a critical role in safeguarding your online security. Here’s why it matters:
- Early Detection of Suspicious Activity: By identifying mismatches between IP and phone number locations, the algorithm helps detect potential unauthorised access attempts or fraudulent activities.
- Preventing Account Compromise: Mismatched locations could indicate an attacker attempting to impersonate you from a different location. The algorithm acts as a vigilant guardian to prevent account compromise.
- Strengthening Online Authentication: Ensuring that IP and phone number locations match enhances the security of authentication, making it harder for unauthorised individuals to gain access.
Browser Safety: AuthSafe Protecting Your Browser from ATO Threats
Browser safety plays a critical role in safeguarding users against ATO (Account Take Over) attacks, which are attempts by malicious actors to gain unauthorised access to user accounts and sensitive information. As users engage with various websites and online services, their web browsers serve as the gateway to the digital world, making them a prime target for cyber threats.
By focusing on browser safety, Authsafe addresses potential vulnerabilities and ensures a secure online experience for its users.
- Mitigating Exploitable Vulnerabilities: Web browsers are complex software systems prone to security vulnerabilities. Attackers often exploit these vulnerabilities to deliver malware, initiate phishing attempts, or execute other malicious activities. By prioritising browser safety, Authsafe can identify and address these vulnerabilities, reducing the risk of successful ATO attacks.
- Protecting Against Phishing and Spoofing: Phishing attacks rely on deceiving users into providing sensitive information through fake websites that appear legitimate. By tracking the latest browser versions and ensuring users have secure browsers, Authsafe can implement robust anti-phishing measures, protecting users from falling victim to such fraudulent schemes.
- Safeguarding Login Credentials: User login credentials are valuable targets for cybercriminals attempting ATO attacks. Secure browsers with up-to-date security patches can effectively protect login information, minimizing the chances of unauthorised access to user accounts.
- Detecting Anomalous Behaviour: Authsafe employs policy signals to track browser activity and detect any anomalous behaviour that may indicate an ATO attempt. By analysing patterns and deviations, Authsafe can take proactive measures to prevent potential security breaches.
- Monitoring for Browser Updates: Staying informed about the latest browser versions is crucial to address emerging threats and vulnerabilities. Authsafe’s commitment to tracking browser updates ensures users are protected with the most secure browsing experience possible.
- Enhancing Overall Cybersecurity: Browser safety is an integral part of Authsafe’s comprehensive cybersecurity strategy. By securing the user’s primary digital interface – the web browser – Authsafe strengthens the overall security posture and creates a resilient defense against ATO attacks.
Incorporating robust browser safety measures is a fundamental aspect of Authsafe’s commitment to safeguarding its users against ATO attacks. By prioritising the protection of web browsers and ensuring their safe usage, Authsafe enables users to navigate the digital landscape with confidence and peace of mind.
OldBrowserVersion: Detecting Outdated Browser Versions
The OldBrowserVersion algorithm is an essential feature of Authsafe, designed to protect users from potential security risks associated with outdated web browser versions. Authsafe diligently monitors the versions of browsers used by its users to ensure their safety online. Let’s explore how this algorithm works and why it matters for you:
- Collecting Browser Information: Authsafe keeps an eye on user activities, especially when they log in or log out. During these events, the algorithm gathers information about the user’s web browser, its version, and the operating system (OS) they are using.
- Version Validation: To ensure maximum security, Authsafe maintains a database of supported browser versions for different operating systems. The algorithm compares the user’s browser version with the latest supported version for their OS.
- Raising an Event: If the user’s browser version is outdated and poses security risks, the algorithm raises an event called “OldBrowserVersion” (OBV) with a designated score indicating the severity of the detection.
- Continuous Monitoring: The OldBrowserVersion algorithm operates in real-time, continually monitoring browser versions. If a user’s browser becomes outdated after login, Authsafe promptly raises an alert to ensure that necessary action is taken.
Why it’s Crucial for You?
Outdated browser versions can expose users to various security threats and potential ATO attacks. Authsafe’s focus on detecting and addressing old browser versions offers the following benefits:
- Enhanced Security: By identifying outdated browser versions, Authsafe ensures that users have the most secure and up-to-date browsing experience. This significantly reduces the risk of vulnerabilities and potential exploitation by cybercriminals.
- Protection Against Exploits: Outdated browsers often lack the latest security patches, leaving users vulnerable to various exploits and attacks. Authsafe’s vigilance in detecting old browser versions helps protect users from these threats.
- Preventing Data Breaches: Security breaches can lead to unauthorised access to sensitive user data. By promptly alerting users to update their browsers, Authsafe minimises the risk of data breaches and unauthorised account access.
TorBrowser Algorithm: Detecting Tor Browsers
The TorBrowser algorithm is a critical component of Authsafe, designed to identify and mitigate potential risks associated with the usage of Tor browsers. Authsafe employs advanced techniques to detect Tor browser traffic and protect users from potential security threats. Let’s delve into the details of how this algorithm works:
- Tor Browser Detection: The TorBrowser algorithm leverages the IP2Tor class, specifically configured in “mode 1,” to identify Tor browser traffic. It retrieves the IP address from the incoming event and checks if it matches any known Tor exit nodes.
- Real-Time Monitoring: Operating in real-time, the algorithm continuously monitors incoming requests for signs of Tor browser usage. Upon detection of a Tor browser, it raises an event called “TorBrowser” (TB) with a designated score indicating the severity of the detection.
- Enhanced Security Measures: When a Tor browser is detected, Authsafe takes necessary security measures, such as flags access, based on the severity of the event.
- IP2Tor Integration: The TorBrowser algorithm integrates the IP2Tor class to efficiently identify and track Tor exit nodes. This integration enhances Authsafe’s ability to protect users from potential ATO attacks facilitated through the Tor network.
Importance of TorBrowser Algorithm in ATO Protection
Detecting Tor browsers is crucial for safeguarding user accounts and preventing unauthorised access. The TorBrowser algorithm’s significance lies in the following aspects:
- Mitigating Anonymity Risks: Tor browsers are often used to mask the identity and location of attackers. By detecting and blocking Tor browser usage, Authsafe reduces the risk of ATO attacks facilitated through anonymous channels.
- Protecting Against Fraudulent Activities: Tor browsers are occasionally employed to perform fraudulent activities, such as fake account registrations or login attempts from untraceable locations. Authsafe’s ability to identify and block Tor browsers significantly reduces the risk of such activities.
- Enhancing Account Security: By proactively detecting Tor browsers, Authsafe adds an extra layer of security to user accounts. This helps prevent unauthorised access attempts and protect sensitive user data from potential breaches.
- Real-Time Alerts: The TorBrowser algorithm’s real-time monitoring ensures that any suspicious Tor browser activity is immediately reported to users. This enables timely response and action to secure user accounts and thwart potential attacks.
DisabledCookies Algorithm: Detecting Disabled Cookies
The DisabledCookies algorithm is an integral part of Authsafe’s security framework, aimed at identifying instances where users have disabled cookies. Cookies play a crucial role in maintaining user sessions and providing personalised experiences. Authsafe actively monitors for disabled cookies to enhance security measures and ensure a smooth user experience. Let’s explore the workings of this algorithm:
- Cookie Status Detection: The DisabledCookies algorithm leverages event information provided by the incoming request to determine the cookie status. It checks if the event is either “login succeeded” or “logout” and examines whether cookies are disabled (indicated by the absence of a “ce” key in the event).
- Real-Time Monitoring: Operating in real-time, the algorithm continuously monitors incoming requests for disabled cookies. If a request indicates disabled cookies during a login attempt or logout, the algorithm raises an event called “DisabledCookies” (DC) with a predefined score reflecting the severity of the detection.
- Enhanced Security Measures: Authsafe responds to the “DisabledCookies” event by applying appropriate security measures. For instance, it may prompt the user to enable cookies to ensure proper functioning and enhanced security.
- User Experience Considerations: While security is paramount, Authsafe aims to maintain a positive user experience. The algorithm strikes a balance between enforcing cookie usage for security reasons and providing a seamless user experience.
Importance of DisabledCookies Algorithm in ATO Protection
Detecting disabled cookies is crucial for both security and user experience aspects of Authsafe.
- Enhancing Session Management: Cookies are essential for maintaining user sessions, enabling users to navigate various parts of the platform without repeated logins. By detecting disabled cookies, Authsafe ensures a smooth session management process, improving user convenience.
- Detecting Unauthorised Activity: Disabling cookies can be a sign of malicious intent or unauthorised access attempts. Authsafe’s ability to identify such instances adds an extra layer of security, helping protect user accounts from potential ATO threats.
- Prompting Security Measures: When disabled cookies are detected during critical operations like login or logout, Authsafe prompts users to enable cookies for secure interactions. This proactive approach aids in mitigating security risks.
- Preventing Account Vulnerabilities: By enforcing cookie usage, Authsafe minimises the risk of vulnerabilities arising from compromised sessions, helping maintain a secure and trusted environment for its users.
- Balancing Security and Experience: While focusing on security, Authsafe strives to deliver an optimal user experience. The DisabledCookies algorithm strikes the right balance, ensuring security measures do not disrupt user interactions or negatively impact user satisfaction.
UnpopularScreenResolution Algorithm: Detecting Unpopular Screen Resolutions
The UnpopularScreenResolution algorithm is an essential component of Authsafe’s ATO detection mechanism, designed to identify users with uncommon or unpopular screen resolutions. By monitoring screen resolutions, Authsafe gains valuable insights into potential security risks. Here’s how the algorithm works:
- Dataframe Selection: The algorithm selects the appropriate dataframe based on the user’s device type (desktop, tablet, or mobile). Each dataframe contains a list of popular screen resolutions for the respective device type.
- Real-Time Screen Resolution Detection: When a user logs in or logs out, the algorithm checks if the provided screen resolution is present in the list of popular resolutions for the specific device type.
- Event Triggering: If the screen resolution is not found in the list of popular resolutions, the algorithm raises an event called “UnpopularScreenResolution” (USR) with a predefined score to signal the potential security concern.
- Enhancing ATO Protection: By identifying users with uncommon screen resolutions, Authsafe adds an extra layer of ATO protection. Unusual screen resolutions may indicate fraudulent activities or unauthorised access attempts.
Importance of UnpopularScreenResolution Algorithm in ATO Protection
The UnpopularScreenResolution algorithm plays a critical role in safeguarding user accounts and detecting potential ATO threats. Here’s why it matters:
- Identifying Anomalous Activities: Uncommon screen resolutions can be indicative of suspicious activities. Authsafe’s ability to detect such resolutions enables it to identify potential ATO attempts or compromised accounts.
- Enhancing User Security: By monitoring screen resolutions, Authsafe ensures that users are using standard and secure screen settings. This proactive approach reduces the risk of vulnerabilities arising from non-standard resolutions.
- Real-Time Protection: The algorithm operates in real-time, continuously monitoring screen resolutions during login and logout events. Real-time detection enables swift response to potential security threats.
- Tailored Detection for Device Types: Authsafe customises the detection process based on the user’s device type (desktop, tablet, or mobile). This targeted approach ensures precise identification of uncommon resolutions specific to each device.
- Data-Driven Insights: The data collected by the UnpopularScreenResolution algorithm provides Authsafe with valuable insights into user behaviours and potential attack patterns. This data-driven approach helps refine security measures and enhances ATO protection strategies.
Take the first step towards a more secure future. Try AuthSafe today and experience the peace of mind that comes with having a robust fraud detection solution by your side.
References
[1] S. Frenkel and M. Isaac, “Facebook reveals data breach affecting 50 million users,” https://www.nytimes.com/2018/09/28/technology/facebook-hack-data-breach.html?auth=register- emailregister=email, 2018, accessed: July 28, 2023.



